Sharing files online is common but can be risky. Sensitive data needs protection.
We often need to share files, whether for work, school, or personal reasons. But how do we ensure our files remain secure during transfer? Cyber threats and data breaches are real concerns. Understanding the best practices for secure file sharing is crucial.
This guide explores easy and effective ways to keep your data safe while sharing it online. You will learn about encryption, secure file-sharing platforms, and tips to protect your information. Let’s dive into the essentials of secure file sharing to keep your data safe.
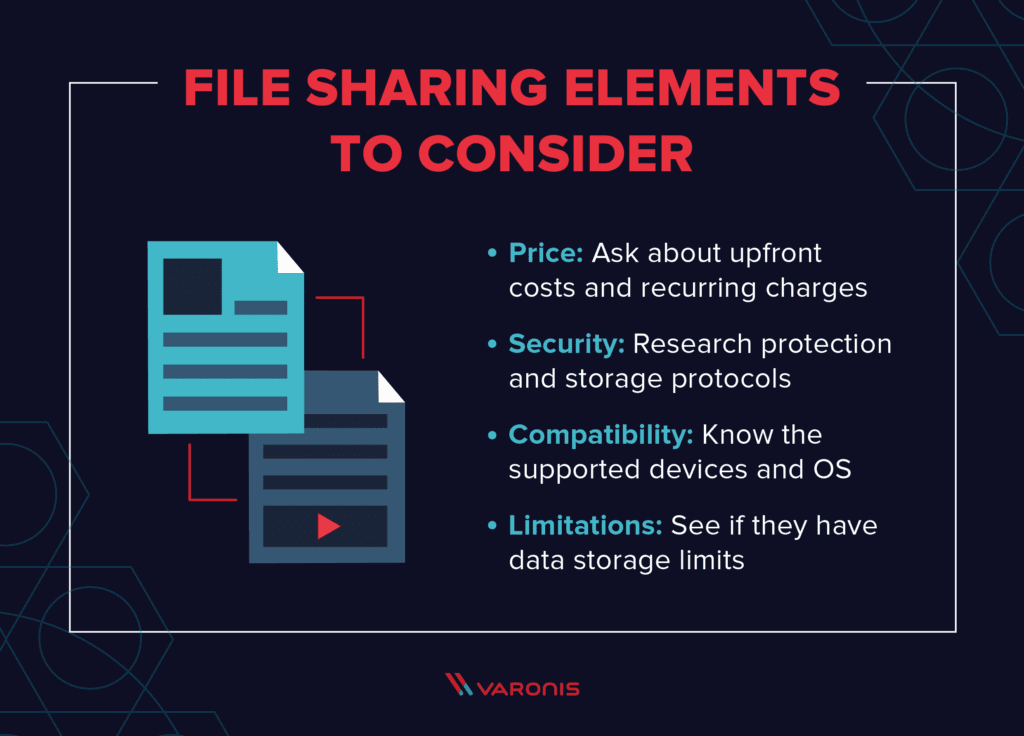
Choosing The Right Platform
Sharing files online can be risky without the right platform. It’s important to choose a secure and reliable service. This section will guide you through popular file-sharing services and compare their security features.
Popular File-sharing Services
Several file-sharing services are widely used. Here are some of the most popular:
- Dropbox: Known for its ease of use and wide adoption.
- Google Drive: Integrated with Google services, offering ample storage.
- OneDrive: Microsoft’s solution, great for Windows users.
- WeTransfer: Simple and quick for sending large files.
- Box: Focuses on business collaboration and security.
Comparing Security Features
Security is crucial when sharing files online. Let’s compare the security features of these popular platforms:
| Service | Encryption | Two-Factor Authentication | Data Loss Prevention |
|---|---|---|---|
| Dropbox | AES 256-bit | Yes | Yes |
| Google Drive | AES 256-bit | Yes | No |
| OneDrive | AES 256-bit | Yes | Yes |
| WeTransfer | AES 256-bit | No | No |
| Box | AES 256-bit | Yes | Yes |
Dropbox and OneDrive offer strong security features, including data loss prevention. Google Drive is secure but lacks data loss prevention features. WeTransfer is great for quick transfers but falls short on advanced security. Box provides robust security, ideal for business use.
Encryption Basics
In the digital age, securely sharing files online has become crucial. One essential method to ensure security is through encryption. This blog section will cover the basics of encryption and how it helps in protecting your sensitive data.
Explore the depths of Cloud Storage and File Sharing with this informative post. Best Free Cloud Storage Options: Top Picks for 2025
What Is Encryption?
Encryption is the process of converting data into a code to prevent unauthorized access. It transforms readable data into a scrambled format. Only authorized parties can decode and access the original data. This ensures that even if someone intercepts the data, they cannot read it.
Types Of Encryption Methods
There are several encryption methods available to secure your data. These methods vary in complexity and security levels. Below are the most common types:
- Symmetric Encryption: Uses the same key to encrypt and decrypt data. It is fast and suitable for large data sets. An example is the Advanced Encryption Standard (AES).
- Asymmetric Encryption: Uses a pair of keys – a public key and a private key. The public key encrypts the data, while the private key decrypts it. This method is more secure but slower. An example is the RSA algorithm.
- Hashing: Converts data into a fixed-size string of characters. It is a one-way process, meaning it cannot be decrypted. It is used for verifying data integrity. Examples include MD5 and SHA-256.
| Encryption Method | Key Used | Speed | Security | Example |
|---|---|---|---|---|
| Symmetric Encryption | Same Key | Fast | Moderate | AES |
| Asymmetric Encryption | Public/Private Key Pair | Slow | High | RSA |
| Hashing | No Key | Fast | High | SHA-256 |
Understanding these encryption methods helps you choose the right one for your needs. Always ensure your data is encrypted before sharing it online. This will protect your sensitive information from unauthorized access.
Password Protection
Sharing files online can be risky. Password protection can help. It adds a layer of security. This makes it harder for unauthorized users to access your files. This section will cover creating strong passwords and using two-factor authentication.
Creating Strong Passwords
A strong password is your first line of defense. Use a mix of letters, numbers, and symbols. Avoid common words and phrases. Make your password at least 12 characters long. Consider using a password manager. It can help you create and store strong passwords.
Dive into Cloud Storage and File Sharing and uncover valuable details in this article. Cloud Storage Comparison Google Drive Vs Onedrive: Ultimate Guide
Two-factor Authentication
Two-factor authentication (2FA) adds extra security. It requires two forms of identification. This could be a password and a code sent to your phone. Even if someone guesses your password, they need the second factor. Enable 2FA on your file-sharing accounts. It makes unauthorized access much harder.
Credit: www.xcitium.com
Using Secure Links
When sharing files online, using secure links is crucial. Secure links help protect sensitive information. They ensure only intended recipients access the files. This method adds an extra layer of security. Below, we explore some effective ways to use secure links.
Time-limited Links
Time-limited links are a great way to share files securely. These links expire after a set period. This minimizes the risk of unauthorized access. For example, you can set a link to expire in 24 hours. After that, the link becomes useless.
Here’s how to create a time-limited link:
- Upload your file to a secure file-sharing service.
- Select the option to create a link.
- Set the expiration time for the link.
- Share the link with the intended recipient.
Using time-limited links ensures that your files are not accessible indefinitely. It’s a simple yet effective security measure.
Access Controls
Access controls allow you to manage who can view your files. You can set permissions to restrict access. For example, you can limit the link to specific email addresses. This ensures only those individuals can open the link.
Here are some common access control options:
| Access Control Option | Description |
|---|---|
| Specific Email Addresses | Only designated email addresses can access the link. |
| Password Protection | Access requires a password you provide. |
| View-Only Access | Recipients can view but not edit the file. |
Implementing access controls adds another layer of security. It ensures only authorized individuals can access your files.
Using secure links with time-limited links and access controls can significantly enhance your file-sharing security. Always consider these options to protect your sensitive information.
Curious about Cloud Storage and File Sharing? This post offers a deeper understanding. Benefits of Using Cloud Storage for Businesses: Boost Efficiency
Avoiding Public Wi-fi
Sharing files online has become a daily necessity. But using public Wi-Fi for this can be risky. Public networks are convenient but often lack security. This can expose your sensitive data to hackers. Let’s dive into why you should avoid public Wi-Fi for file sharing.
Risks Of Public Networks
Public networks are open to everyone. This makes them a hotspot for cybercriminals. Hackers can easily intercept data shared over these networks. Your personal information can be stolen in seconds. Even seemingly harmless data can be used against you.
Most public networks do not use strong encryption. This leaves your data vulnerable. Anyone with the right tools can access your files. You might not even know your data has been compromised. Always be cautious when using public Wi-Fi.
Using Vpns For Security
A Virtual Private Network (VPN) can help secure your data. VPNs encrypt your internet traffic. This makes it harder for hackers to intercept your files. Even on public Wi-Fi, a VPN can provide a layer of protection.
Choose a reliable VPN service. Free VPNs might not offer strong security features. A good VPN can safeguard your online activities. It can also mask your IP address, adding another layer of privacy. With a VPN, you can share files securely, even on public networks.
Using a VPN is simple. Most services offer easy-to-use apps. Connect to the VPN before accessing any public Wi-Fi. This small step can make a big difference in protecting your data. Secure your file sharing with a trusted VPN.
Regular Software Updates
Regular software updates are crucial for keeping your online files secure. They fix vulnerabilities, enhance performance, and offer new features. Ignoring updates can leave your files exposed to threats. Keeping your software up-to-date is an essential step for safe file sharing.
Importance Of Updates
Software updates are critical for several reasons. First, they patch security vulnerabilities. Hackers look for weaknesses in outdated software to exploit. By updating, you close these gaps.
Second, updates often include performance improvements. They make your software run faster and more efficiently. This can speed up file transfers and enhance your overall experience.
Third, new features can be added with updates. These features can make file sharing easier and more secure. Don’t miss out on these benefits by ignoring updates.
Automating Updates
Manually updating software can be a hassle. Fortunately, you can automate updates to make the process easier. Here’s how:
- Go to your software settings.
- Find the update section.
- Enable the automatic updates option.
Automating updates ensures that you are always protected. It also saves time and effort. Here’s a quick reference:
| Step | Description |
|---|---|
| 1 | Access software settings |
| 2 | Locate the update section |
| 3 | Enable automatic updates |
By following these steps, you can ensure your software is always up-to-date. This helps keep your files secure.
Verifying Recipients
In the digital age, sharing files is a common task. But, ensuring that these files reach the right hands is crucial. Verifying recipients is a step often overlooked. This simple step can prevent unauthorized access and protect sensitive information. Here, we will explore key methods for confirming the identity of your recipients.
Confirming Identities
Confirming identities is the first step in securely sharing files online. Always know who you are sending files to. Use known contacts or addresses. If unsure, ask for a quick video call. A call can confirm the recipient’s identity.
You can also use two-factor authentication. Send a code via email or text. The recipient must enter this code to access the file. This step ensures that only the intended person can open the file.
Using Secure Communication Channels
Using secure communication channels is essential. Avoid public Wi-Fi when sending files. Public networks can be unsafe. Use a secure network or a Virtual Private Network (VPN). A VPN masks your IP address. This makes your connection more secure.
Choose encrypted services for sharing files. Some services offer end-to-end encryption. This means only you and the recipient can read the files. Examples of such services include Signal and ProtonMail.
Here is a table of secure communication channels:
| Service | Encryption Type |
|---|---|
| Signal | End-to-End |
| ProtonMail | End-to-End |
| End-to-End |
Always choose secure channels for file sharing. This simple step can save your sensitive data from falling into the wrong hands.
Monitoring File Access
Monitoring file access is a crucial part of securely sharing files online. It ensures that only authorized individuals can view, download, or modify the shared files. By keeping an eye on who accesses your files and how they use them, you can protect sensitive information and maintain privacy.
Tracking Downloads
Keeping track of downloads helps you understand who is accessing your files. This is especially important for confidential documents. Tracking downloads allows you to see the number of times a file is downloaded and by whom.
- Download logs: Maintain logs of all download activities. This log should include the IP address, timestamp, and user credentials.
- Real-time alerts: Set up alerts to notify you when a file is downloaded. This way, you can act immediately if unauthorized access is detected.
- Usage reports: Generate regular reports to review download activities. These reports help you identify any unusual patterns.
Revoking Access
Revoking access is a key aspect of maintaining control over your shared files. It allows you to withdraw permissions from users who no longer need access or who have violated your terms.
- Time-limited access: Set expiration dates for file access. This ensures that access is automatically revoked after a certain period.
- Manual revocation: Manually revoke access for specific users. This is useful when you need to immediately block someone.
- Access control settings: Use access control settings to easily manage permissions. Adjust these settings as needed to maintain security.
| Feature | Description |
|---|---|
| Download Logs | Records of all download activities with user details. |
| Real-time Alerts | Notifications sent when a file is downloaded. |
| Usage Reports | Regular reports showing download patterns. |
| Time-limited Access | File access expires after a set time. |
| Manual Revocation | Immediate removal of user access. |
| Access Control Settings | Settings to manage and adjust permissions. |

Credit: www.makeuseof.com
Frequently Asked Questions
How Can I Share Files Securely Online?
To share files securely online, use encrypted file-sharing services. These services protect your files with encryption, ensuring only the intended recipient can access them.
What Are The Best Secure File-sharing Methods?
The best secure file-sharing methods include using encrypted email services, cloud storage with encryption, and secure file transfer protocols (SFTP).
Are Cloud Storage Services Secure For File Sharing?
Yes, many cloud storage services offer strong encryption. Services like Google Drive and Dropbox include built-in security features to protect your files.
How Do I Encrypt Files Before Sharing?
To encrypt files before sharing, use encryption software like VeraCrypt or BitLocker. These tools ensure your files remain protected during transfer.
Conclusion
Securing files online is crucial for privacy. Use trusted platforms to share. Always encrypt sensitive documents. Strong passwords add extra protection. Regularly update your sharing methods. Stay aware of new security trends. Educate yourself on potential risks. Sharing files can be safe with the right steps.
Keep your data protected and share responsibly. Your privacy matters. Happy sharing!